This blog was originally published here by Mohamed Ibrahim
Hello Amazing Hackers… Mohamed Ibrahim is Here
This is my first Article and we will talk about how I was able to bypass the admin panel and login to Admin dashboard on one of the public bug bounty program
Lets call our program redacted.com for privacy. First I start my recon process with some shodan dorking like: org:"redacted" || ssl:"redacted.com" and play with filters like: http.title || port, till I found an ip that was running on port 8080 and has a basic auth.
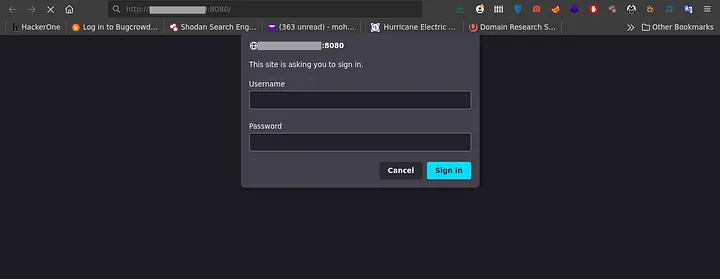
Now lets try to bypass it..
1. Default Credentials
In this situation, first thing I do is check for default credentials like:
admin:admin
admin:password
user:user
but nothing worked here, searched on google for default credentials of the panel name but nothing found.
But when I saw the Authentication failure error on the panel:
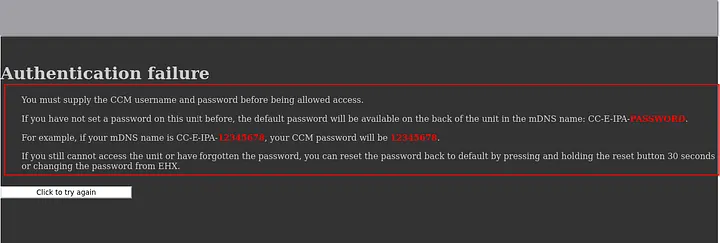
I thought that the username and the password is a default credentials comes with the product|application installed here. It something like PIN-CODE or Serial Number or Product Number|Version. Like WiFi device in your home, it comes with default PIN-CODE.
2. Directory Fuzzing
I moved to the next step, and used fuff for Directory Fuzzing with my custom wordlist that get me some interesting results :
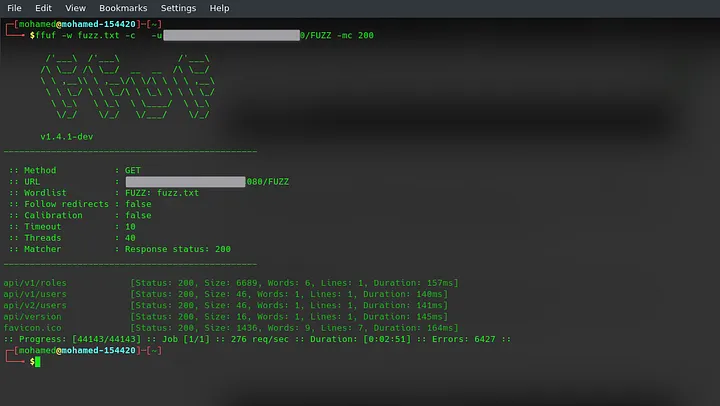
I go to http://<ip>:8080/api/v1/roles/ but found nothing then I go to http://<ip>:8080/api/v1/users/ and found the only username of the panel!
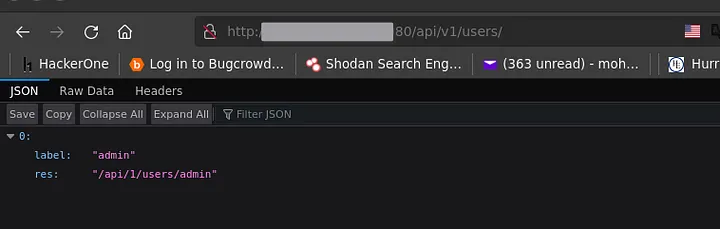
Now we have the username, lets see what we can do with it
3. Brute Forcing
I fired up my Burp Suite to capture the login request for brute forcing attack. I entered username:admin & password:12345678 and capture the request:
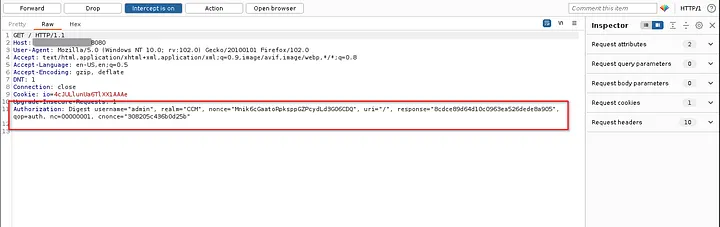
The request has an Authorization header with the credentials . I can see the value of the username(admin) but can not see the password value(12345678) that I entered . Seems the application make some kind of Encryption(I don’t know). so I can’t do brute force attack.
Back to the Directory Fuzzing again to get some more result. This time I start fuzzing under /api/v1/ directory and get some new result :
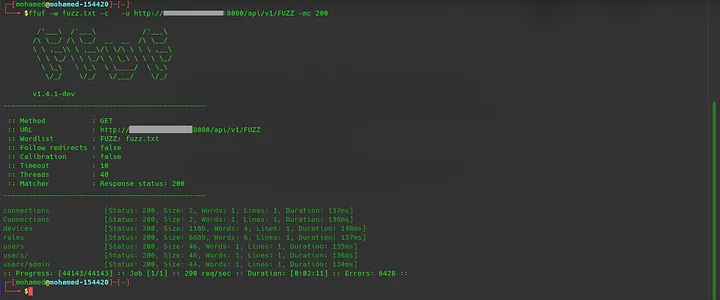
OK, Lets go to http://<ip>:8080/api/v1/devices/
I open the above url and again found nothing. but wait, I found another directory: /api/v1/devices/snapshot
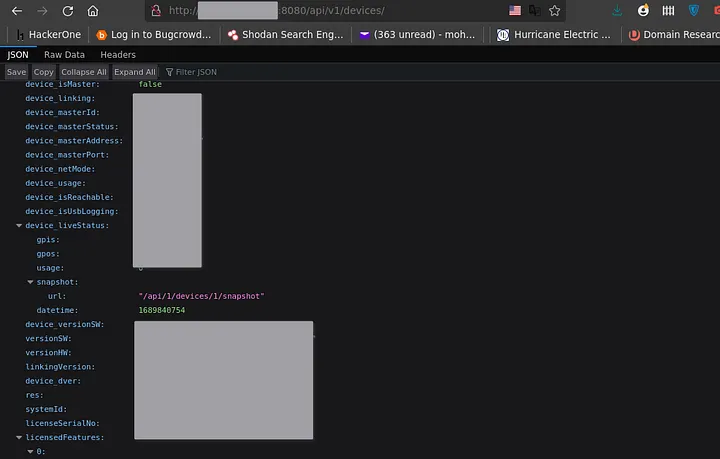
I go to http://<ip>:8080/api/1/devices/1/snapshot and it was a downloaded file(compressed). I open it and take a round in it.
I opened every file searching for something useful till I found this file /tmp/hw_info.txt . From it’s name ,it seems it has some information about the product|Application:
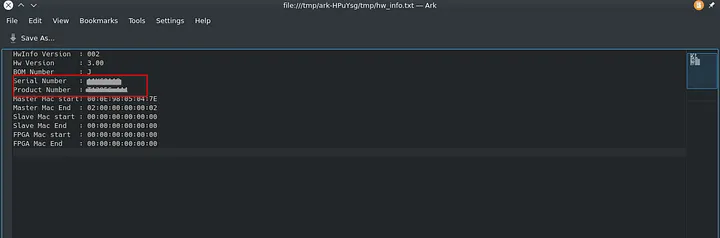
The file has Serial Number & Product Number of the product|Application.
I though that why not use those numbers as a password for the username(admin)..?? Lets give a try… Back to login with:
user:admin & pass:<Product number> -> Username||password is wrong
user:admin & pass:<Serial number> -> ( BooOooM )Login Successful ..
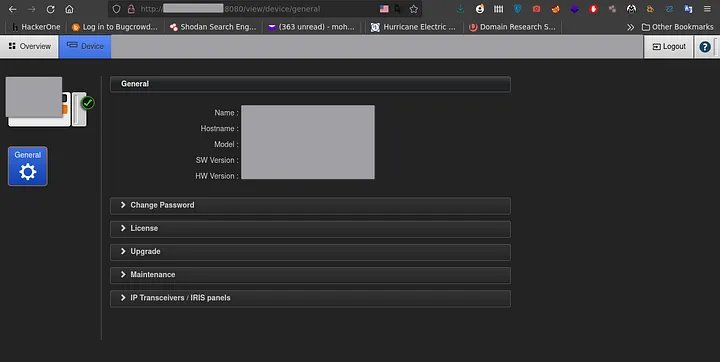
I Immediately write a good report mentioned the above steps and sen it to the program on hackerone.
Fortunately, I didn’t get Duplicated …And my report Triaged as a Resolved(CRITICAL).
Thank you Amazing Hackers for reading my writeup.
For any FAQ or any FeedBack, I’m here:
Twitter LinkedInTo add your blog, send an email to hello@bugbountydirectory.com