Hello Hackers, Ram Ram Bhyi Sarya Ne
Hope you’re doing great. This is V3D, sharing a quick write-up with my friend Gaurav Gajre on one of our recent findings “Unauthorised Access to 80k+ User Data via Chatbot Signup.”
Note: This was on a private Bug Bounty Program, so I can’t reveal the actual program name. Let’s call it REDACTED.COM.
Without any further ado… let’s buckle up.

So once upon a time, one of my best buddies, Oxdln, found a vulnerability in a Bugcrowd public program. He found an IP, and when he opened it, there was a login page. He just tried admin: admin, and boom, he was logged in. He reported it and bagged a $2500 bounty. When he told me this, I was like - bro, when will I ever find something like this? He just said: “It’s all about being at the right place at the right time.” That line always stayed with me. And that’s pretty much where this story begins. Big shoutout to all my broskis who always have my back.
Fast forward, Gaurav bhai and I were grinding on this private program for 18 days straight. Found a bunch of medium and low issues, but no critical or high. Then we thought, let’s run waybackurls on REDACTED.COM. That’s when we stumbled upon a URL we hadn’t seen before:
https://terabot.redacted.com/homeWe opened it, and it showed us a signup page.
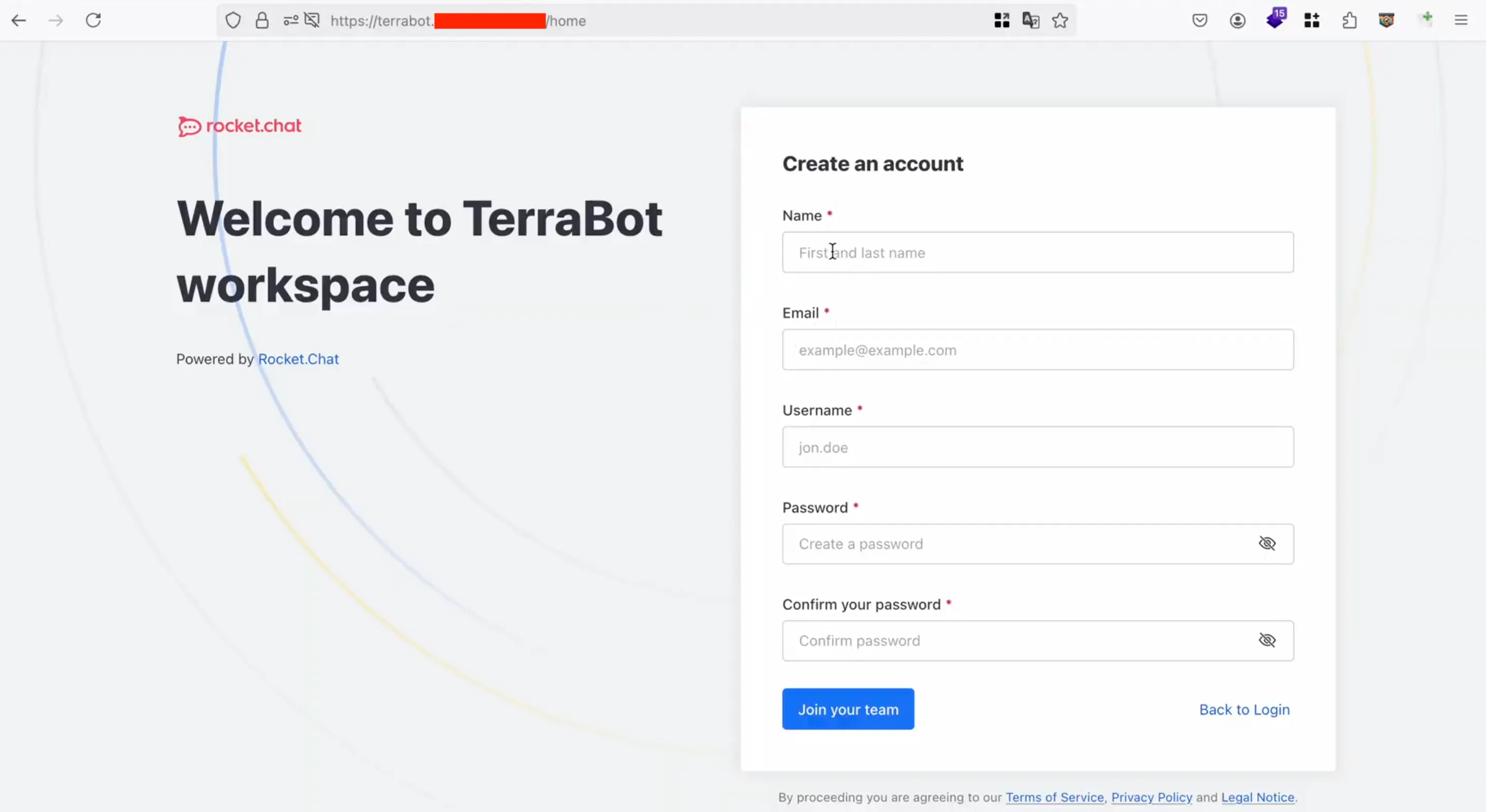
We filled in the details and hit “Join your team.” To our surprise, we were directly logged into the application without any verification. Looked fishy, so we started digging deeper into every functionality.
And then we struck a gold mine, an “Omnichannel Contact Center” directory.
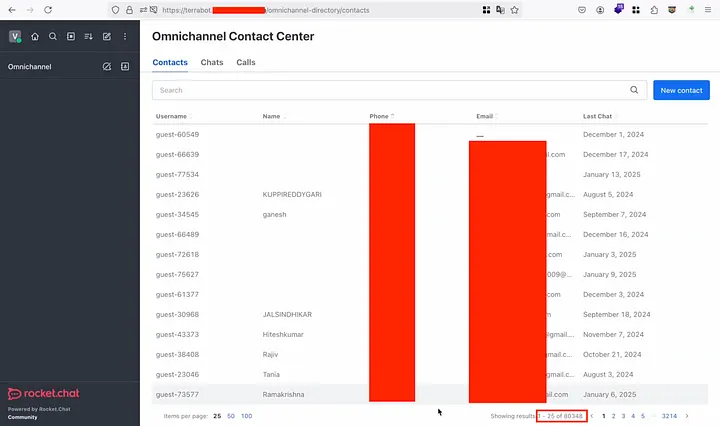
Inside it, we found 80k+ user records including username, name, email, and phone numbers. Not just that, we could even create chatbot support agent accounts and interact with live super agents.
Our reaction:

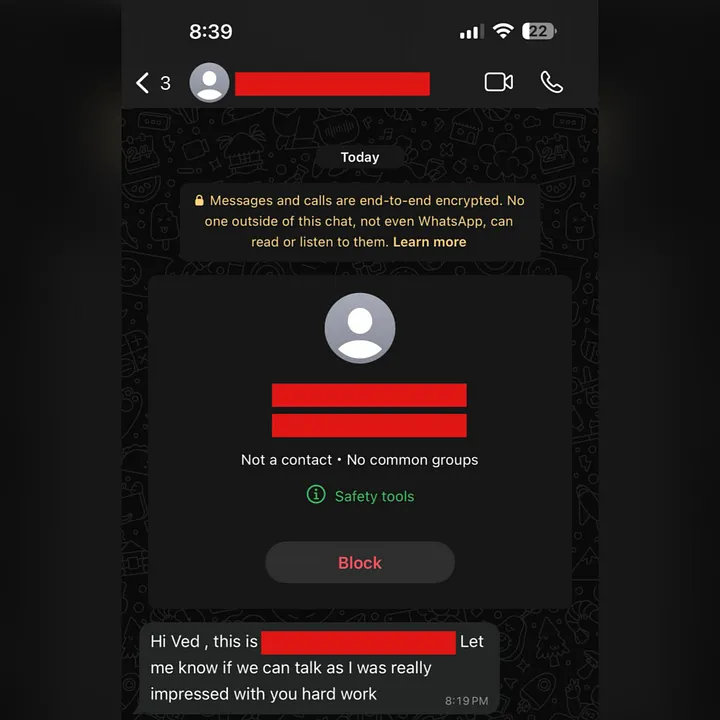
We quickly prepared our report and sent it over. The team first accepted it as High, but we knew this was beyond High. We requested a re-evaluation. Even the company’s VP (Vice President) reached out to me directly on WhatsApp, encouraging our efforts.
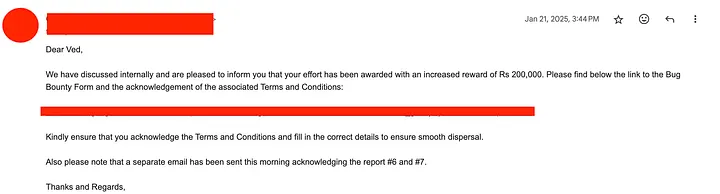
After three days, we got the final reply, they reclassified it as Critical and increased the bounty amount.
And that’s how a random signup page turned into access to 80k+ users’ data. Right place, right time. Hope you find this write-up helpful.
Hope you learned something new. If you like the write-up and follow me on X(Twitter) and LinkedIn






