This blog was originally published here by Dewanand Vishal
This is a story about how I found my first SQL injection (SQLi) bug in a private program. Although I’m not new to this field, finding SQLi has become challenging due to the implementation of new types of web application firewalls (WAFs). I’m always curious when someone discovers a SQLi vulnerability nowadays and shares it on Twitter. Before we delve into the story, let’s understand what SQL injection is.
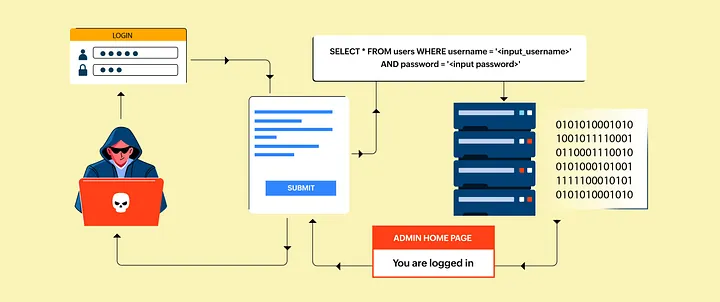
SQL injection (SQLi) is a type of attack that exploits vulnerabilities in web applications that use SQL databases. Attackers inject malicious SQL code into input fields, tricking the application into executing it. This can allow them to gain unauthorized access to sensitive data, modify or delete data, or even take control of the database server.
Where is the bug ?
One of the private programs at Intigriti. I was testing a health product website for low hanging fruits then I found a BMI calculator. I provide input height and weight, capture that request and send it to the repeater. I noticed that when I put ‘ (single quote) in the unitWeight parameter in the request body and got a 500 error response, I put another ‘ (single quote) to fix the query and the error disappeared. Now it’s time to prove that SQLi is possible here. I tried a few payloads and got a payload response with a time delay.
Payload: ‘XOR(if(now()=sysdate(),sleep(10),0))XOR’Z
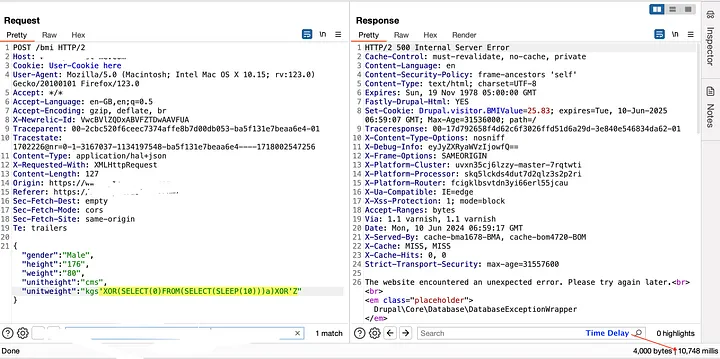
Then I reported it to security team, they confirmed the vulnerability and fixed the issue and rewarded.
Where to find ?
- Form fields: Any input field where users can enter text, numbers, or other data, such as login forms, search bars, or comment sections.
- URL parameters: Values passed in the URL after a question mark (?), such as ?id=1.
- Cookies: Data stored on a user’s computer that can be sent to the server with each request.
- HTTP headers: Information sent from the client to the server as part of an HTTP request.
- POST Request: Data sent to the server within the body of an HTTP POST request. This data often includes parameters and identifiers.
Pro Tips:
When searching for SQL vulnerabilities, browse every feature of the application. Try to actively trigger error messages, as these can often reveal underlying database interactions.
Feel free to send me dm in twitter @dewcode if you want to know more about this bug.
Happy Hacking
To add your blog, send an email to hello@bugbountydirectory.com