How I Found a Critical Password Reset Bug in the BB program(and Got $4,000)
This blog was originally published here by Imran Hossain
As a bug bounty hunter, I often test mobile apps by routing traffic through Burp Suite to see how the backend APIs behave. One of my recent hunts led me to an interesting endpoint in the BB Parents app that turned into a serious vulnerability.
Finding the Endpoint:
I extracted the endpoints from the JavaScript files and built a custom wordlist. Then I used FFUF with that wordlist to perform fuzzing.
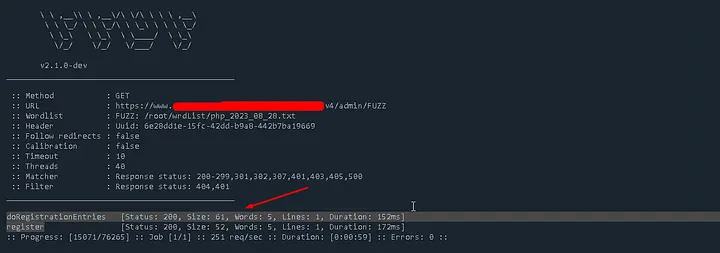
- While testing the Android app, I noticed a request to this endpoint: https://www.redact.com/parents/application/v4/admin
- Naturally, I decided to fuzz the endpoint. By appending random words and observing responses, I eventually discovered: https://www.redact.com/parents/application/v4/admin/doRegistrationEntries

At first glance, it looked like an endpoint for new user registration. I confirm that this is for new registration.
The Bug
Here’s where things got interesting. This endpoint didn’t just allow new account creation — it also let me overwrite the password of any existing account without verifying if the email was already registered. In simple terms:
- If a user already had an account, sending their email + a new password to this endpoint would reset their password.
- Their existing data and profile remained untouched; only the password changed.
That meant I could take over any parent’s account just by knowing their email address.
Reproducing the Issue
The reproduction steps were very straightforward:
- Intercept a request from the mobile app in Burp Suite and get the endpoint.
- FUZZ THE endpoint https://www.redact.com/parents/application/v4/admin/FUZZ
- Modify the endpoint to: https://www.redact.com/parents/application/v4/admin/doRegistrationEntries
- When I hit the Send Button, Response said to
Only POSTrequest is allowed. - I switched to the post method and changed the header,
Content-Type: application/jsonand got the are asking for two required parameters.
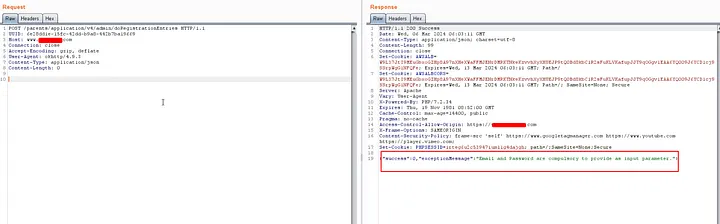
- Replace the email field with the victim’s email, and set any new password.
{"email":"victim@example.com","password":"New@12345"}
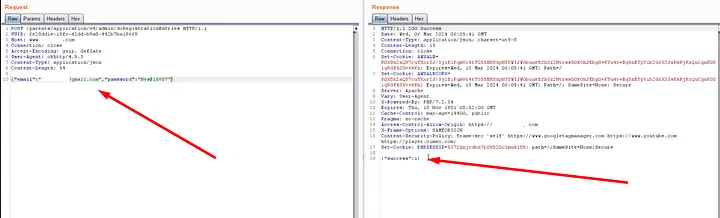
- The response came back with
success: 1, and now I could log in to the victim’s account.
Impact
This was a critical authentication bypass. Any parent’s account could be hijacked with just their email address.
Considering that the Program is used for student safety, parent communication, and school monitoring, the impact was very high.
Reporting & Reward
I reported the bug responsibly through the H1 BB program. The team at Redact was very responsive, acknowledged the issue quickly, and fixed it.
As a token of appreciation, I received a $4,000 reward for this finding.
Key Takeaways
Always fuzz API endpoints — hidden functions often reveal themselves this way.
Registration endpoints can sometimes double as password reset mechanisms.
Simple parameter manipulation (like email + password) can lead to critical account takeover issues.
Always report responsibly so that users stay protected. Happy Hunting - https://x.com/s41n1k
To add your blog, send an email to hello@bugbountydirectory.com

