Hello Researchers,
Welcome back to my Medium blog! I’m excited to see you here and can’t wait to share more inspiring content with you.
Story Behind This XSS: As a Microsoft Most Valuable Researcher (MVR) for both 2024 and 2025, I spend most of my time exploring and hunting for vulnerabilities through the MSRC Bug Bounty Program.
Part 1: Identifying the Vulnerability
While searching my name on Google using keywords like “Niraj MSRC,” I came across a Microsoft blog post (https://www.microsoft.com/en-us/msrc/blog/2024/08/congratulations-to-the-msrc-2024-most-valuable-security-researchers) where I was listed in 3rd position among the MSRC 2024 Most Valuable Security Researchers — recognized as one of the top Dynamics 365 researchers!
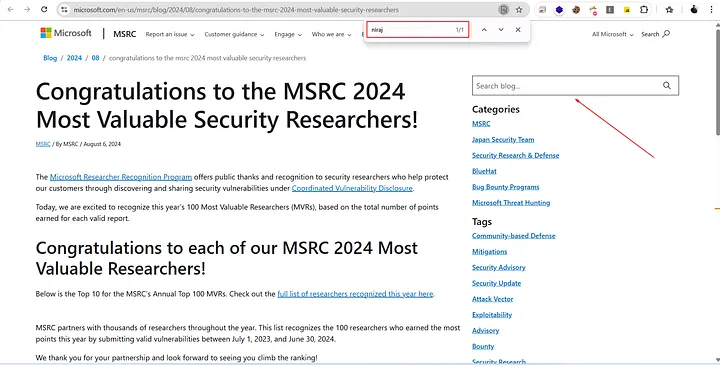
On this Microsoft blog page, there’s a search bar that allows users to look up blogs. Out of curiosity, I searched for my name again 😄 — and noticed that it was being reflected directly on the page.
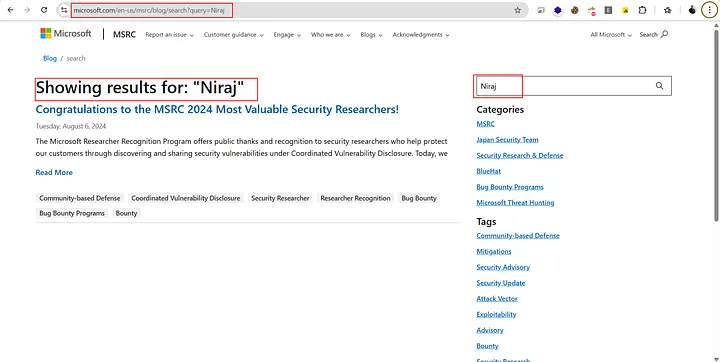
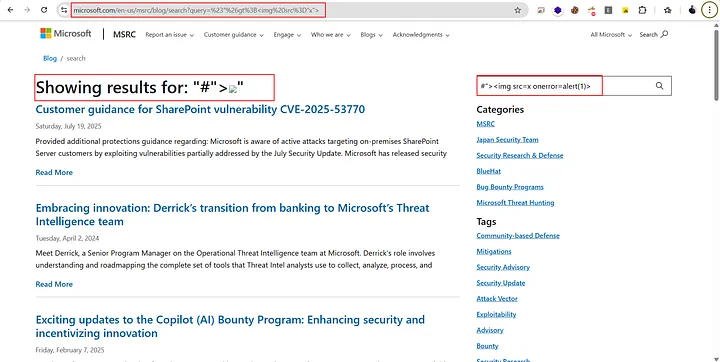
The first thing that came to my mind was XSS. I tried multiple payloads, but none of them worked — some were blocked by the WAF. After a few more attempts, I noticed a broken image appearing on the page, which confirmed that the “query” parameter was vulnerable to HTML injection and could potentially be escalated to an XSS vulnerability. Below is the payload I used:
#"><img src="x" onerror="alert(1)" />Notice that the > (greater-than) character in the URL is being HTML-encoded, and all event handlers (for example, onload and onerror) are being removed.
• • •
Part 2: Exploiting the Vulnerability
I tried HTML injection using basic HTML tags and XSS, but I couldn’t get any JavaScript to execute due to the WAF.
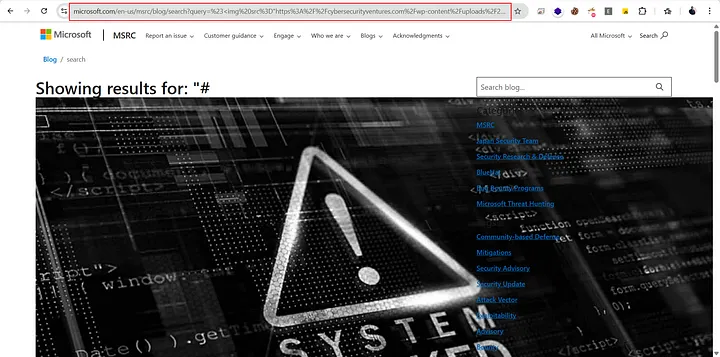
After trying a bunch of things for 2–3 hours, I eventually managed to trigger the XSS. I started with the search bar, but everything was being filtered so I put the payload straight into the URL and used a basic XSS payload. To my surprise, the <script> tag worked.
#<script>alert(document.domain);</script>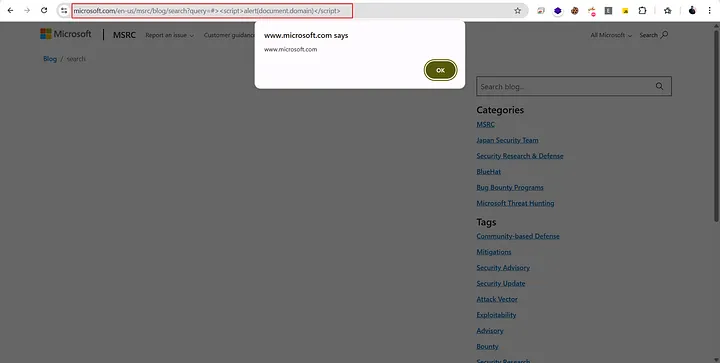
When you’re facing a WAF, it’s sometimes necessary to change your approach. Here is the final reflected XSS URL:
https://www.microsoft.com/en-us/msrc/blog/search?query=#%3E%3Cscript%3Ealert(document.domain)%3C/script%3ESometimes you need to change your approach when you are dealing with WAF.
Disclosure Timelines
- Oct 6, 2025: Vulnerability discovered.
- Oct 6, 2025: Reported through MSRC portal.
- Oct 8, 2025: Status moved to Review/Repro.
- Oct 11, 2025: Confirmed by MSRC; status moved to Develop.
- Oct 15, 2025: Microsoft has confirmed the fix, and the status has been updated to Complete.
- Oct 15, 2025: Draft blog post sent to MSRC for review.
If you need any help or want to connect, you can connect with me via LinkedIn and Twitter .
I hope it will help you in your Bug Hunting !!
Thanks for Reading !!😊
./Keep_Hacking






