Hey there, Brace yourselves for a tale of code capers, bounty hunting, and a surprisingly sweet $500 reward, all set in the enchanting realm of Reddit. Grab your virtual popcorn — it’s storytime!
Understanding CSRF
Think of it as the digital world’s version of a sneaky prankster — Cross-Site Request Forgery (CSRF) is the name. Imagine someone making wishes on your behalf without your permission. I stumbled upon this mischievous glitch in Reddit’s armor, a vulnerability waiting to be unraveled.
Discovery and Exploration
Picture me, a curious digital explorer, venturing into the mysterious landscape of Reddit. With nothing more than a keyboard and a thirst for discovery, I began a quest to uncover any weak spots in Reddit’s online defenses. As I delved deeper, I stumbled upon a hidden pathway that opened the door to a trove of vulnerabilities yet to be discovered.
Based on a Hypothetical Scenario, Here’s How the Adventure Unfolded
- Logged in: I donned my digital explorer’s hat and entered Reddit, credentials in hand.
- Hidden Portal: A hidden passage caught my eye — a ticket to comment manipulation.
- Innocent Code: Crafting a seemingly benign comment deletion request.
- The Ingenious Setup: I set my trap — a cleverly disguised webpage under my control, waiting for an unsuspecting visitor.
- The Presto Change-o: A click later, the code sprang into action, leveraging their session to vanish a comment.
- Abracadabra! Proof of Concept: Like a digital prestidigitator, I made a comment disappear before their very eyes. Behold — the proof of concept was complete!
<html>
<body>
<script>
history.pushState("", "", "/");
</script>
<form action="https://www.redditgifts.com/comments/delete/`id`/">
<input type="submit" value="Submit request" />
</form>
</body>
</html>Responsible Disclosure
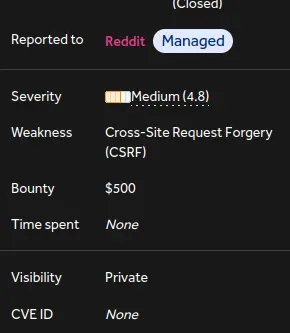
With a heart pulsating with cautious excitement, I reached out to Reddit’s security team. And then, at the pinnacle of our collaboration, a virtual treasure chest was opened, revealing a coveted bounty of $500.
Lessons Learned
As I reflect on this expedition, vital lessons come to the fore. Never underestimate the potential of seemingly simple bugs. In the labyrinth of complex vulnerabilities, it’s easy to overlook the straightforward ones. They might appear unassuming, but they often hold the key to unlocking the bounty.
Wrapping Up the Hacky Fiesta!
With the curtain gently falling on this chapter, the story of my Reddit bounty and CSRF discovery finds its denouement. From the maze of vulnerability to the exhilarating $500 prize, the journey echoed the adage that sometimes, simplicity holds the grandest rewards.
Please feel free to share this write-up with aspiring bug hunters, encouraging them to embark on their own bug bounty quests.
Find me on Twitter: @a13h1_






