Hi mates, I’m Mahmoud — aka brbr0s. I’m a bug hunter who’s always trying to learn more and get better at what I do. I’m mainly focused on red teaming fields and hope to go deeper in this track specifically in the future. In this blog, I’ll be sharing some of the bugs I find and the things I learn along the way.
First of all, we attribute all grace to Allah; without Him, we would not have been guided, nor given charity, nor prayed. Let’s get started

Now, here’s my last finding. I will demonstrate how I, as a collaborator, can Access Owner’s Bank Account Information via Response Manipulation in BBP on Bugcrowd.
As usual, I started with the user settings, and the target didn’t have a lot of functionality to test.
What caught my attention is “Bank account info” endpoint, with this one the owner can add and view his bank’s info, good. Another function I noticed that, the owner can invite a collaborator to be added on the same account.
After invite myself to the my owner account as a collaborator, I tried to access Bank account info endpoint but I faced:


As usual, ‘No’ is the most green flag for bug hunters.
After analyzing the burp history, I noticed this interesting endpoint:
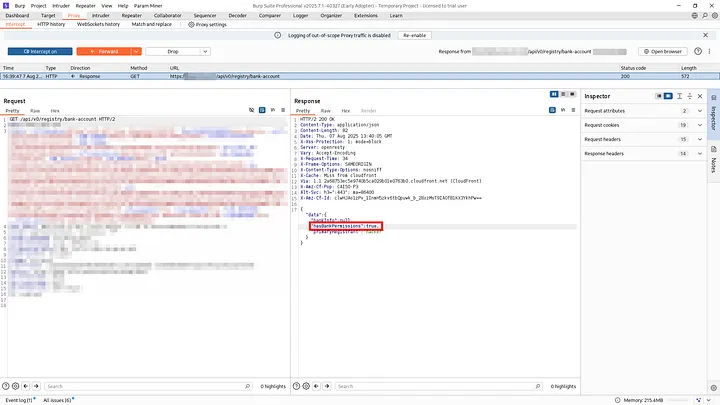
/api/v0/registry/bank-accountwith this data in the response:
"data": {
"bankInfo": null,
"hasBankPermissions": false,
"primaryRegistrant": "hacker"
}
hasBankPermissions, interesting huh!!
What If I intercept the request and change hasBankPermissions value in the response from false -> true !!
Let's tryyy…
Forward it…
I can modify the owner’s bank account information and worse, I can access data which already he entered.
As I noticed, It’s one between 10 endpoints in the user setting page, a little bit haa?!!
So I predicted the duplicate rushing towards me, but I won’t lose anything if I report it.
Annnnd as expected, it hit me 3 days after, Alhamdulillah.
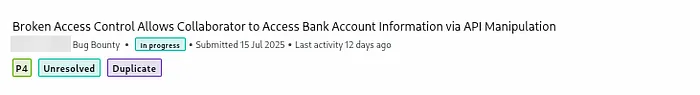
Stay tuned for the coming valid one
Let’s connect on X
To add your blog, send an email to hello@bugbountydirectory.com


